
Unmasking Fake CEO and Other Email Phishing Tactics
We all laughed heartily when James Veitch told his story (scroll below for video) of working with a spammer to ‘sell gold’. But most phishing

We all laughed heartily when James Veitch told his story (scroll below for video) of working with a spammer to ‘sell gold’. But most phishing

If you’re looking to buy a laptop that works well for personal and business use, know that you’re in the majority. This is a common

Businesses today rely on a plethora of IT infrastructure. From emails to critical client data, all are reliant on a vast network of interconnected devices.

At the time of writing of this article, Facebook is on the verge of launching its own currency, Libra – no doubt, with some (ironic)

Have you experienced network security problems that have cost your small to midsize business valuable time and money to fix? In our hyper-connected world, it

Malware is one of the single biggest risks businesses face today. Why? It’s because the confidential client and financial information, customer databases, business strategies, and
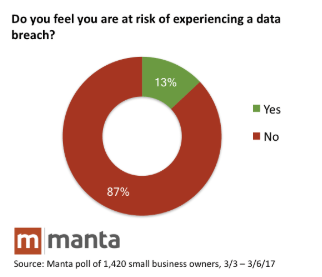
Businesses today are more dependent on their technology than at any time in history. New technologies have created a wealth of opportunities for entrepreneurs and

As business owners, we see the headlines every day. Data breaches aren’t going away and hackers are getting better at their jobs. That’s why safeguarding

If your business is like most today, you rely heavily on technology to accomplish your work. You have also spent a great deal of time

Hackers are starting to forgo “big scores” that are harder to accomplish, and have been moving on to ultimately easier thefts from smaller and medium-sized